802.1X - IEEE-802 authentication¶
This howto describes the configuration and use of the IEEE 802.1X authentication for Surf-LAN clients in combination with an IACBOX.
Attention
Do not confuse this with the 802.1x settings found on the network settings page - this is used when the IACBOX has to authenticate itself at a switch.
Hint
- The network devices used (WiFi access point, router, switches) must support IEEE 802.1X
- Client devices also need to have this type of authentication implemented (for WiFi this is often called WPA Enterprise)
- The IACBOX currently supports the EAP-TTLS and PEAP variants.
How does 802.1X work?¶
IEEE 802.1x is a network security procedure which forces client devices to authenticate themselves before they get access to a local network. The protocol used is EAP (Extensible Authentication Protocol) and is the core of IEEE 802.1x and allows the exchange of authentication messages on layer 2.
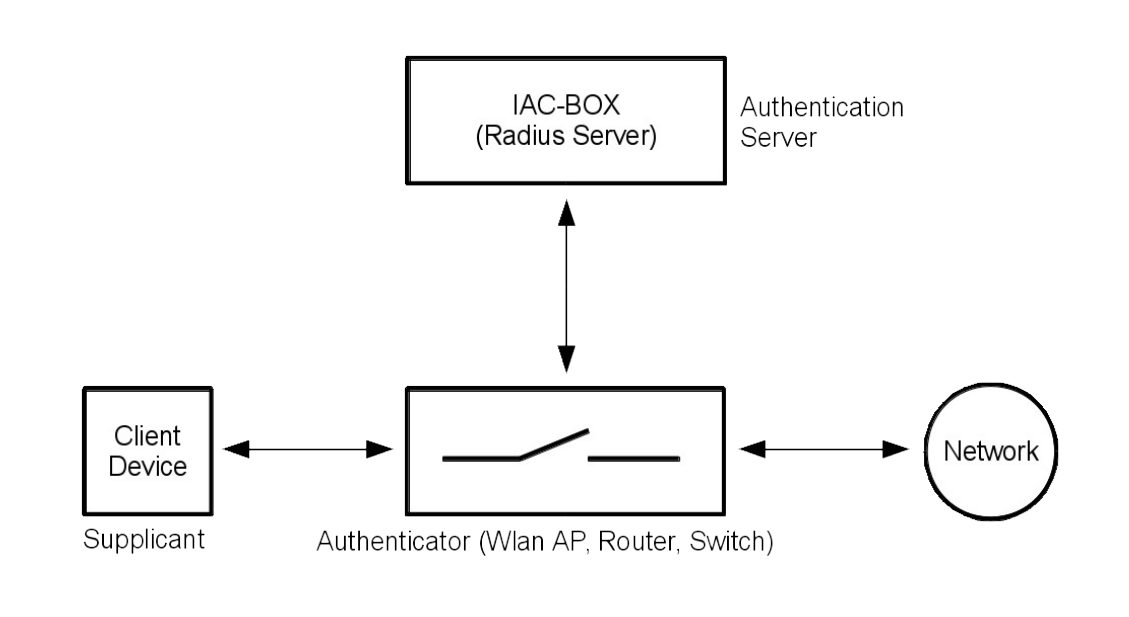
Components of an IEEE 802.1x network are the supplicant devices, authenticator devices and the authentication server.
The authentication server validates the request of the supplicant devices and notifies its decision to the authenticator. Based on this, the authenticator grants or denies access to the local network for the supplicant device.
- Supplicant Device - WiFi Clients, LAN-Stations
- Authenticator Devices - WiFi-Access-Points, Router, Switches
- Authentication Server - Radius-Server, LDAP-Gateway/Server
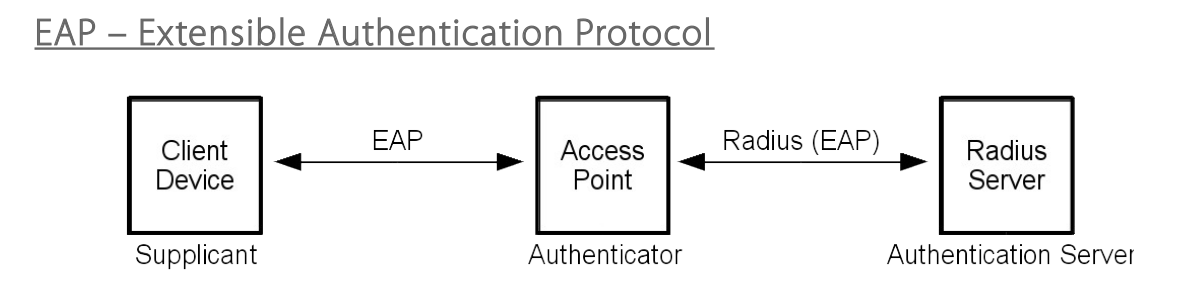
The communication between supplicant and authenticator is done with EAP and for the communication between authenticator and authentication server, EAP packets are encapsulated in radius packets. Since the original EAP is not very safe, there are advanced EAP variants that provide additional security. For example with EAP-TTLS and PEAP (protected EAP), an own tunnel from each supplicant device to the local network is established.
IEEE 802.1X and IACBOX¶
If IEEE 802.1x is used in combination with the IACBOX, the IACBOX is used as authentication server. Thereby the IACBOX works as radius-server for the authentication clients.
Configuration on the IACBOX¶
You can activate the IEEE 802.1x authentication in the WebAdmin menu Security/General of the IACBOX.
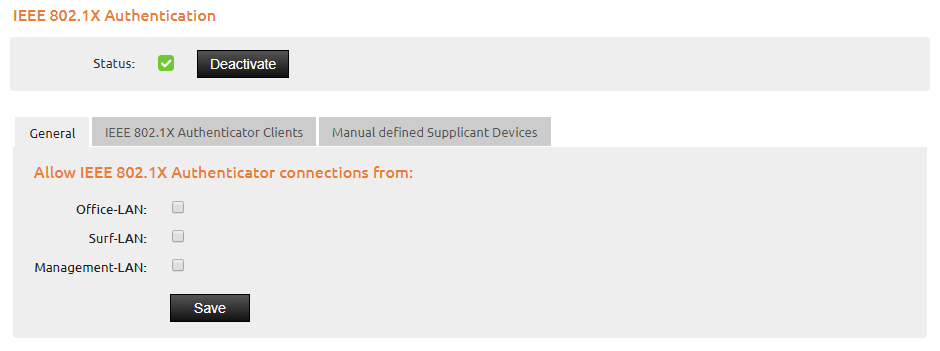
First of all, you need to select the networks (Office-LAN, Surf-LAN, Management-LAN) where authenticator clients are accepted from.
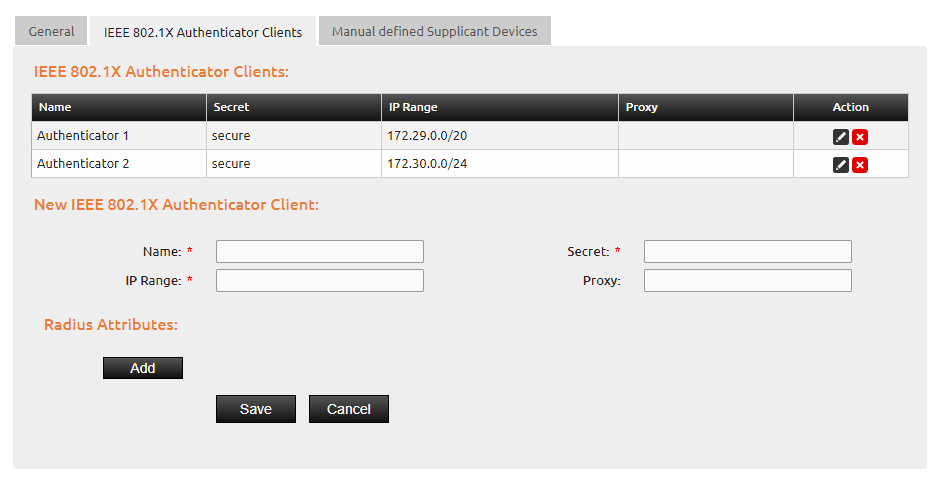
Next, all authenticator clients which should be connected to IACBOX need to be defined in the tab IEEE 802.1x Authenticator Clients. Please note, that the secret needs to coincide with the configured secret on the authenticator client. Otherwise there is no communication possible between both devices. The mandatory IP-address range means that only supplicant devices (client devices) with an IP-address within this range are allowed to authenticate.
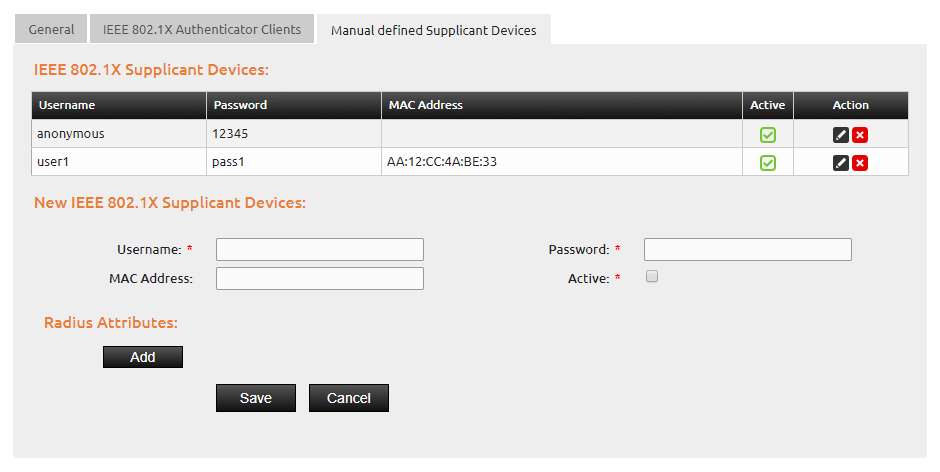
In addition, you can add allowed supplicant devices and general 802.1x users manually. You can add individual supplicant devices with their MAC- addresses. This means the userdata defined can only be used by the supplicant device with the associated MAC-address. If the MAC-address field is left blank (general 802.1x user), all supplicant devices can authenticate with the defined user data.
All other supplicant devices (client devices) which are not defined manually, can authenticate via 802.1X by using WebAdmin Tickets of the IACBOX. The authentication with Ext-Auth users (MySQL, PostgreSQL, MSSQL) and local users is also possible, but associated with limitations.
Example Configuration 1 - Two-stage logon¶
In the WebAdmin of the IACBOX, manually define a general 802.1X user for all supplicant devices (leave the MAC-address field blank). Thus, supplicant devices have access to the network only after authenticating with the manually defined 802.1X user. This means, that after 802.1x authentication, devices get to the IACBOX logon page and need to authenticate again in order to get online.
Example Configuration 2 - Instant logon¶
Instant logon means that the supplicant device (client device) does not need to authenticate twice, once for the 802.1x procteded network and once at the IACBOX, in order to go online. Instead, with entering the user data (username & password) at the 802.1x authentication, the device will also be taken online immediately by the IACBOX. This can be used with multiple logon methods of the IACBOX:
- WebAdmin Tickets: Use the ticket username and password for the 802.1x authentication.
- WebAdmin Local Users: Use the defined username and password of the local user for the 802.1x authentication.
- WebAdmin External Authentication: Any supported external authentication method that stores the password in clear-text (necessary) can be used for the 802.1x authentication. This includes SQL databases and Radius servers that are used for external authentication by the IACBOX.